Sponsored by Splunk
Sponsored by Splunk
The Guide to Modern APM: Essentials for Your Cloud-native Journey
Sponsored by Splunk
5 Things to Consider When Choosing an APM Tool
Sponsored by Splunk
GigaOm Cloud Observability Report
Sponsored by Splunk
A Beginner's Guide to Kubernetes Monitoring
Sponsored by CrowdStrike
The Total Economic Impact™ Of CrowdStrike Falcon Complete
Sponsored by Qualys Inc.
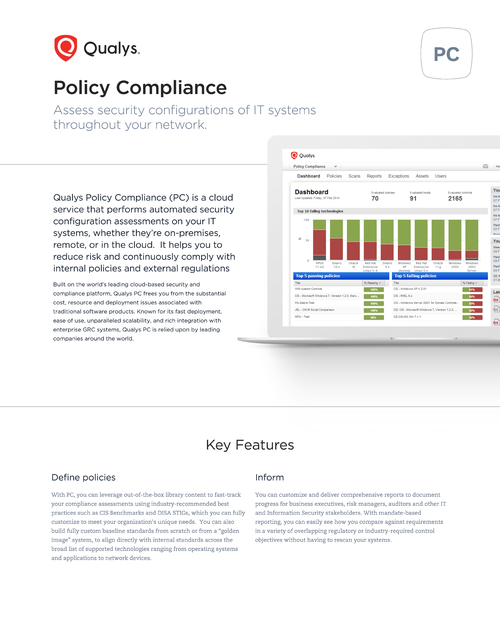
Cloud Based Security & Policy Compliance
Sponsored by Qualys Inc.
An All-in-One Vulnerability Management, Detection, and Response Solution
Sponsored by Qualys Inc.
VMDR: All-in-One Vulnerability Management, Detection & Response
Sponsored by Fortinet
The SD-WAN Executive Check List | 7 Key Steps to Successful Secure SD-WAN Deployment
Sponsored by TrueFort
Real-Time Application and Cloud Workload Protection
Sponsored by RangeForce
Why Cybersecurity Training has Changed Forever
Sponsored by RangeForce
How 400 Barclays Security Professionals Upgraded their Cyber Skills
Sponsored by RangeForce
Making the Business Case for Cyber Skills Training
Sponsored by Sophos