Sponsored by Noname Security
API Security 101 Whitepaper
Sponsored by Whitesource
The Quickest Way to Vulnerability Remediation
Sponsored by Whitesource
The Importance of SBOMs in Protecting the Software Supply Chain
Sponsored by Splunk
Partnering to Achieve Maturity in Zero Trust
Sponsored by Microsoft
India's PDP Bill: The Cybersecurity Implications
Sponsored by Splunk
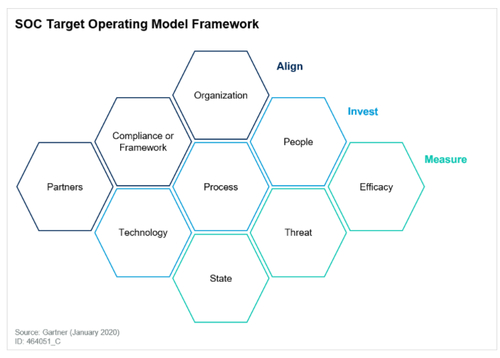
Gartner® Report: Create an SOC Target Operating Model to Drive Success
Sponsored by Splunk
4 Lessons of Security Leaders for 2022
Sponsored by Splunk
Case Study: Slack Unlocks Data to Empower Collaboration
Sponsored by Splunk
How Security Can Fast-track Your Cloud Journey
Sponsored by Splunk
A Guide to Embracing a Zero Trust Security Model
Sponsored by Splunk
Monitoring Your Network in a Cloud-Native Environment
Sponsored by Splunk