Cybercrime , Fraud Management & Cybercrime , Fraud Risk Management
InfoWars: Magecart Infection Points to 'Industrial Sabotage'
Controversial Website Blames Malware on Democrats, China and Big Tech
InfoWars' website was briefly affected by the Magecart payment card skimming malware, a finding that triggered a fiery response from the far right commentary site led by Alex Jones.
See Also: Is Your Email Security Keeping Up with Attackers? Protecting your Microsoft 365 Investment
Security consultant Willem de Groot, who is based in the Netherlands, tweeted on Wednesday that he found Magecart within InfoWars' web shop, which sells a variety of vitamin supplements and survival gear.
Alex Jones busted by real info war. I found a magecart skimmer on the infowars store. Jones blames "leftist US intelligence agencies" #infowars #magecart https://t.co/fA6wiNRvhl
— Willem de Groot (@gwillem) November 14, 2018
De Groot runs internet-wide scans to detect Magecart infections, which often target Magento e-commerce software. The JavaScript-based malware collects payment card and sends the data to another server. The malware is either implanted directly into a Magento installation or sometimes slipped into other third-party tools used on websites.
The stolen payment card data is then likely resold on underground markets, where other scammers try to use the details in card-not-present fraud schemes.
'Industrial and Political Sabotage'
Efforts to reach InfoWars about the incident weren't immediately successful. But the publication ZDNet says it informed InfoWars about de Groot's findings. InfoWars released a statement calling the attack "an act of industrial and political sabotage."
InfoWars says that around 1,600 customers may have been affected. Some of those were returning customers, who may have not needed to enter their personal and card details again, potentially saving them from the malware.
"We use some of the top internet security companies in the nation, and they have reported to us that this is a zero-day hack probably carried out by leftist stay-behind networks hiding inside U.S. intelligence agencies."
—InfoWars
InfoWars' profile grew in recent years as its right-leaning political views and conspiracy yarns gained a growing audience in a changing U.S. political climate. One of the items in its online store is a bumper sticker that says "9-11 Was An Inside Job," referring to the Sept. 11, 2001, terrorist attacks. The store also offers a bumper sticker claiming that fluoride in tap water is poison.
But InfoWars' edgy content has resulted in a rough ride this year. After intense public pressure, platforms including Facebook, Twitter, Apple and Google's YouTube and PayPal moved to ban InfoWars, citing content that violated those service's terms of service.
InfoWars claimed the malware infection is part of efforts to marginalize the site, but it didn't offer any evidence for its assertion.
"Bottom line: This latest action is a concerted effort to de-platform Infowars by big tech, the communist Chinese, and the Democratic party who have been publicly working and lobbying to wipe Infowars from the face of the earth," according to the statement, which ZDNet published in full.
InfoWars says that a report claiming the infection occurred due to a tainted Magento plugin was untrue because it never used the plugin. "We use some of the top internet security companies in the nation, and they have reported to us that this is a zero-day hack probably carried out by leftist stay-behind networks hiding inside U.S. intelligence agencies," Infowars states.
Don't Be InfoWars. Don't Get Infected.
Security experts say that at least seven cybercriminal groups may be behind the wave of Magecart infections, which have affected thousands of e-commerce sites and major companies, including British Airways, Newegg and Ticketmaster (see: RiskIQ: Ticketmaster Hackers Compromised Widely Used Tools).
In September, de Groot warned that Magecart was infecting as many as 50 to 60 e-commerce sites a day. He found that more than 7,300 websites had been infected in the six months up to September, and over 40,000 since he first started scanning in 2015.
A report released earlier this week from the security companies Flashpoint and RiskIQ counts many more victims. The report says that just one hacking collective, referred to as Group 5, has compromised as many as 100,000 organizations and websites (see: Magecart Cybercrime Groups Harvest Payment Card Data).
Magecart: One in Five Victims Gets Reinfected
On Monday, de Groot reported that one in five online stores that suffered a Magecart infection cleaned it up, only to be re-infected. One victim was re-infected 18 subsequent times.
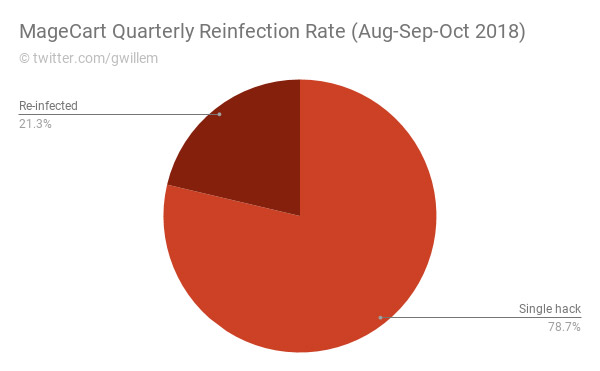
De Groot said these reinfections were thanks to four factors: Magecart attackers growing more sophisticated, including littering an infected site "with backdoors and rogue admin accounts"; using automatic reinfection mechanisms; employing obfuscation techniques to disguise attack code; and exploiting zero-day flaws to install malicious code.
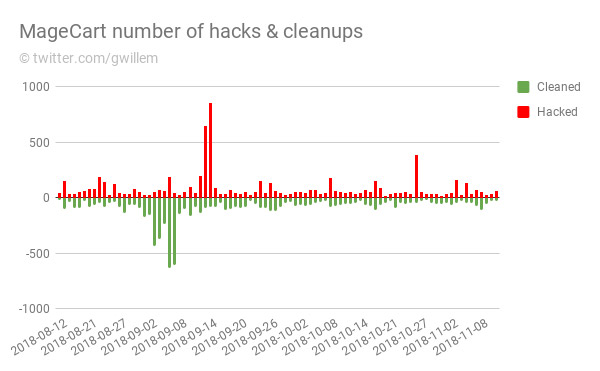
Timing may also pose a problem for some victims. Magecart hackers appear to work mostly on weekends, de Groot says, while victims' IT teams do the bulk of their cleanup efforts during normal working hours.
Magento Scanner
One piece of positive news, however, is that there is plenty that organizations can do to avoid Magecart.
De Groot has developed a scanner for Magento that includes signatures for malware that has targeted the software. The scanner is available on Github.
A service called MageReport from Byte, a Dutch IT services provider, scans for vulnerabilities in Magento. But it's a passive scanner looking from the outside, so it doesn't have access to the code. MageReport can also scan common third-party Magento tools.
In light of the skimming issues, Magento, which is owned by Adobe Systems, has made moves to strengthen security. It has a free service, called Security Scan, that can check patch levels and configuration settings. Users can set it to scan Magento at regular intervals.
(Executive Editor Mathew Schwartz contributed to this story.)





















