Feds Indict 7 Russians for Hacking and Disinformation
Russian Military Intelligence Team Allegedly Conducted Close-Access Operations
See related story: Dutch and British Governments Slam Russia for Cyberattacks
The U.S. Justice Department on Thursday unsealed a criminal indictment that charges seven Russian citizens and residents with computer hacking, wire fraud, identity theft and money laundering.
The indictment by a grand jury in the Western District of Pennsylvania accuses the men of perpetrating "persistent and sophisticated computer intrusions" against multiple targets in the U.S. and abroad meant to promote the strategic interests of the Russian government.
All are alleged members of the Russian Main Intelligence Directorate, aka the GRU.
"We are indicting seven GRU officers for multiple felonies each, including the use of hacking to spread the personal information of hundreds of anti-doping officials and athletes as part of an effort to distract from Russia's state-sponsored doping program," said U.S. Attorney General Jeff Sessions. The defendants in this case allegedly targeted multiple Americans and American entities for hacking, from our national anti-doping agency to the Westinghouse Electric Company near Pittsburgh."
The indictment says five of the GRU officers serve in the elite military unit 26165 - also called GRU 85 Main Special Service Center - which allegedly runs high-risk cyber espionage operations:
- Aleksei Sergeyevich Morenets, 41
- Evgenii Mikhaylovich, Serebriakov, 37
- Ivan Sergeyevich Yermakov, 32
- Artem Andreyevich Malyshev, 30
- Dmitriy Sergeyevich Badin, 27
The indictment also names two other alleged GRU officers:
- Oleg Mikhaylovich Sotnikov, 46
- Alexey Valerevich Minin, 46
"The actions of these seven hackers, all working as officials for the Russian government, were criminal, retaliatory and damaging to innocent victims and the United States' economy, as well as to world organizations," said FBI Director Christopher Wray.
The British and Dutch governments have tied military unit 26165 to attempts to interfere in investigations being conducted into not just into Russia's athlete doping program but also the investigation into the shooting down of Malaysian airlines flight MH17.
"Unit 26165 seems to be quite old, as far as we can tell from the open sources available," Andrei Soldatov, an expert on Russian cyber operations, tells The Daily Telegraph. "It has probably existed since the '70s, and was known as a unit dealing with cryptography."
Each of the seven defendants has been charged with one count of conspiracy to commit computer fraud and abuse, which carries a maximum sentence of five years in prison, and one count each of conspiracy to commit wire fraud and conspiracy to commit money laundering, each of which carries a maximum sentence of 20 years. Five of the suspects - Morenets, Serebriakov, Yermakov, Malyshev, and Badin - have also been charged with two counts of aggravated identity theft, which carries a maximum sentence of two years in prison. Yermakov has also been charged with five counts of wire fraud, which carries a maximum sentence of 20 years.
Intelligence experts say it's unlikely any of the men will ever appear in a U.S. courtroom (see Political Play: Indicting Other Nations' Hackers).
Yermakov, Malyshev, and Badin were already indicted in July by the Justice Department for allegedly conspiring to interfere in the 2016 U.S. presidential election. That indictment named for the first time Russian military unit 26165 as well as its commander in 2016 as being Viktor Borisovich Netyshko (see 10 Takeaways: Russian Election Interference Indictment).
Close-Access Operations
Officials have accused the hackers of not only launching remote attacks, but in some cases traveling abroad to conduct close-access operations, including at the Rio de Janeiro 2016 Summer Olympic Games.
On Thursday, the Dutch government said that its intelligence agents seized specialized equipment from the men that was designed to hack into computer networks or target individuals via their WiFi connections, including hotel WiFi.
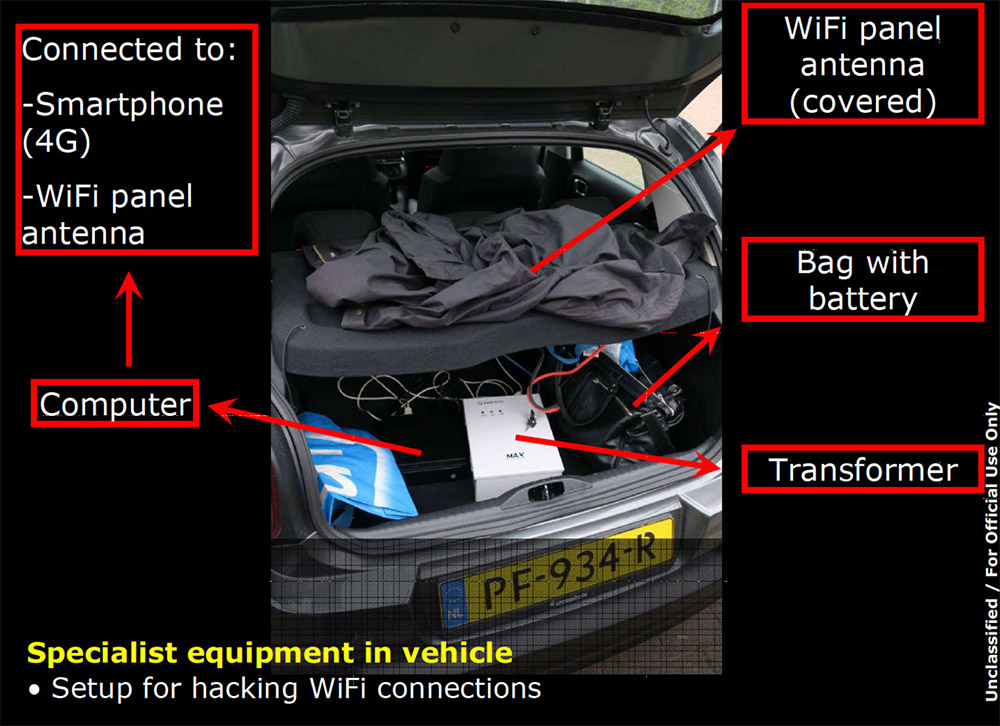
"In April 2018, Morenets, Serebriakov, Sotnikov, and Minin, all using diplomatic passports, traveled to The Hague in the Netherlands in furtherance of another close access operation targeting the Organization for the Prohibition of Chemical Weapons (OPCW) computer networks through WiFi connections," the U.S. Justice Department says.
"All four GRU officers intended to travel thereafter to Spiez, Switzerland, to target the Spiez Swiss Chemical Laboratory, an accredited laboratory of the OPCW which was analyzing military chemical agents, including the chemical agent that the United Kingdom authorities connected to the poisoning of a former GRU officer in that country," it says, referring to 66-year-old Sergei Skripal.
All four alleged Russian agents, however, were later detained by Dutch intelligence agents and expelled from the country. "As part of this disruption, [Morenet and Serebriakov] abandoned the WiFi compromise equipment, which they had placed in the trunk of a rental car parked adjacent to the OPCW property," the Justice Department says.
Dutch investigators said that after reviewing the equipment, they found it had been used for operations around the world, including connecting to a WiFi network at a hotel in Kuala Lumpur, Malaysia, in December 2017, as well as a network used by officials from the Canadian Centre for Ethics in Sport at a Swiss hotel in September 2016, which resulted in the theft of a senior CCES official's credentials.
"Other conspirators thereafter used the stolen credentials to compromise CCES's networks in Canada, using a tool used to extract hashed passwords, the metadata of which indicated it was compiled by Badin," the Justice Department said.
Dutch investigators said that on the laptop of Serebriakov, an alleged GRU "cyber operator," they found a picture showing that he'd been in Rio de Janeiro on Aug. 14, 2016, attending the Summer Olympic Games.

Leak of WADA Data
The alleged GRU agents' activities included not only hacking, but also leaking information via social media and other channels, prosecutors allege.
In the case of one World Anti-Doping Agency leak, the Justice Department says that "the conspirators exchanged e-mails and private messages with approximately 186 reporters in an apparent attempt to amplify the exposure and effect of their message."
Around Aug. 10, 2016, an individual claiming to be from Anonymous contacted Information Security Media Group, sharing a file that containing WADA data and an MP4 video that starts with text being typed: "Today we will show you how we [expletive] wada and some other sites."
ISMG chose to not publish the information.
One month later, confidential drug-testing results for four U.S. Olympic athletes began appearing online.
Shortly thereafter, WADA said that in early August 2016, the Tsar Team - aka APT28 and Fancy Bear - had accessed its Anti-Doping Administration and Management System database after stealing the password assigned to Yuliya Stepanova, who "was the key whistleblower for WADA's Independent Pound Commission that exposed widespread doping in Russian athletics" (see Hackers Dump US Olympic Athletes' Drug-Testing Results).
Spear-Phishing Campaigns
The Justice Department indictment says that the GRU operatives' alleged targets included not only WADA but also the International Court of Arbitration for Sport, known as TAS/CAS. The indictment charges GRU operatives with obtaining spoofed domain names that looked like legitimate WADA and TAS/CAS infrastructure and sending spear-phishing emails to victims at both organizations, as well as at the United States Anti-Doping Agency. The indictment says these spear-phishing attacks successfully compromised employees at both WADA and USADA.
On Wednesday, the FBI obtained a court order and seized two alleged GRU domains - fancybears.net and fancybears.org - "in an effort to limit further exposure of the private lives of victim athletes," the Justice Department says.






















